Why Cryptography? What is here to learn? Is it hard to understand? Is it related to Cryptocurrency?? I know some of you might have these questions in mind. I will briefly explain about these questions. Here we go..
First of all Encryption is essentially important because it secures data and information from unauthorized access and thus maintains the confidentiality.
What is Cryptography?
Cryptography is a method to secure communication from an unauthorized party. Cryptography allows the following 3 goals to be achieved:
Confidentiality: Cryptography protects the secrecy of information. Even if the transmission or storage medium has been compromised, the encrypted information will be render useless to unauthorized person.
Integrity : Cryptography ensures the information has not been tampered with using hashing method.
Authenticity : Cryptography ensures the information sent is from intended and not fake sender. This is done using digital certificate, digital signature and Public Key Infrastructure (PKI).
Didn't understand yet...? Let's take an example
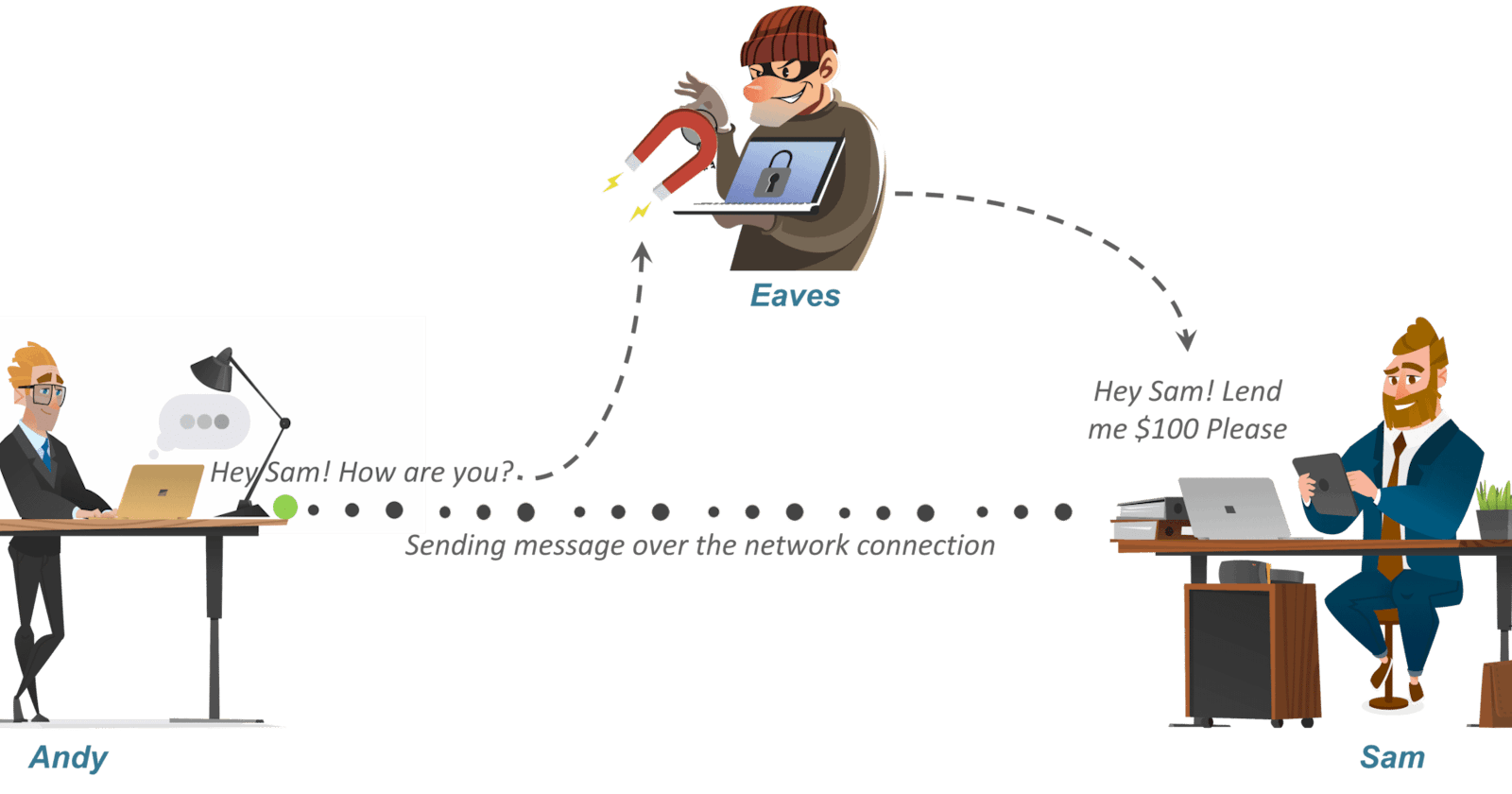
Let’s say there’s a person named Andy. Now suppose Andy sends a message to his friend Sam who is on the other side of the world. Now obviously he wants this message to be private and nobody else should have access to the message. He uses a public forum, for example, WhatsApp for sending this message. The main goal is to secure this communication.
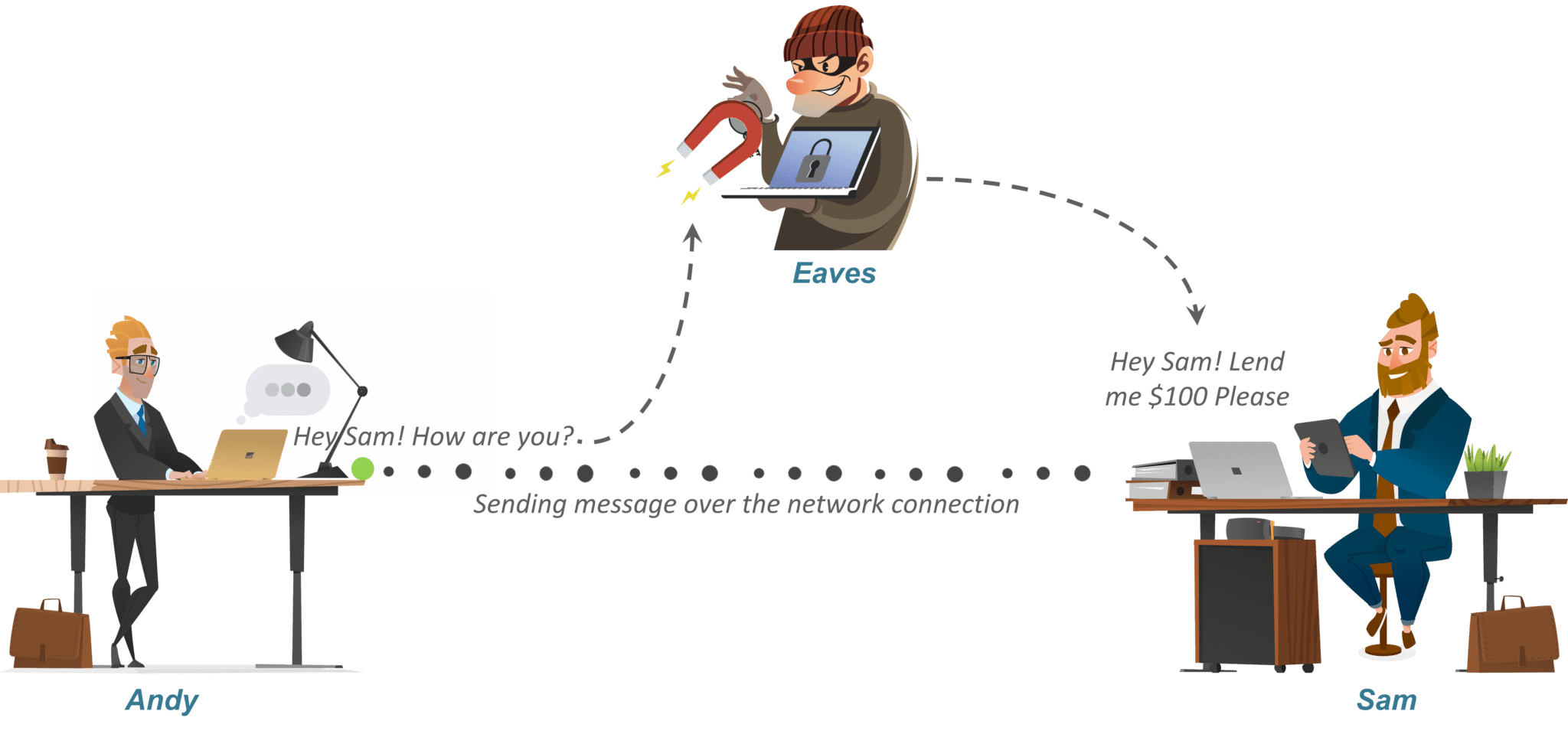
Let’s say there is a smart guy called Eaves who secretly got access to your communication channel. Since this guy has access to your communication, he can do much more than just eavesdropping, for example, he can try to change the message. Now, this is just a small example. What if Eave gets access to your private information? The result could be catastrophic.
So how can Andy be sure that nobody in the middle could access the message sent to Sam? That’s where Encryption or Cryptography comes in.
Now that you guys know What cryptography is, let’s see how cryptography can help secure the connection between Andy and Sam.
Now, Sam would need a key to decrypt the message to recover the original plaintext. In order to convert the ciphertext into plain text, Sam would need to use the decryption key. Using the key he would convert the ciphertext or the numerical value to the corresponding plain text.
After using the key for decryption what will come out is the original plaintext message, is an error. Now, this error is very important. It is the way Sam knows that message sent by Andy is not the same as the message that he received. Thus, we can say that encryption is important to communicate or share information over the network.
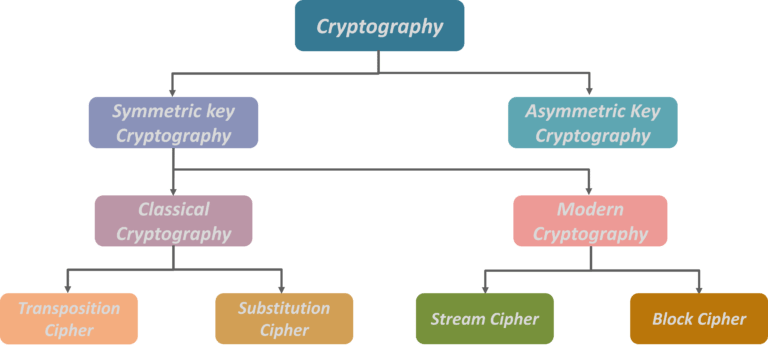
Now, based on the type of keys and encryption algorithms, cryptography is classified under the following categories:
Cryptography can be further divided into:
- Symmetric (or Secret Key) Cryptography
- Asymmetric (or Public Key) Cryptography
Here we will mostly talk about Symmetric and Asymmetric Cryptography.
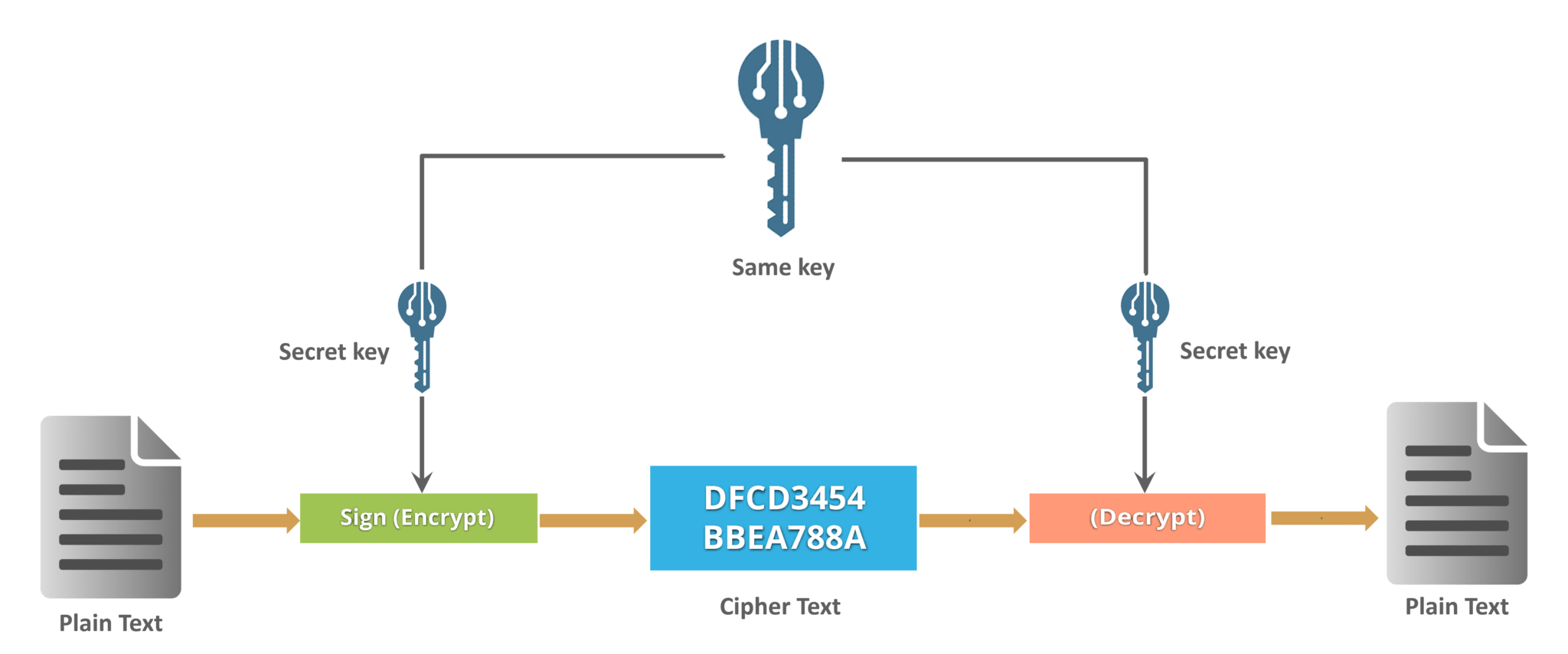
Symmetric Key Cryptography:
An encryption system in which the sender and receiver of a message share a single, common key that is used to encrypt and decrypt the message. The most widely used symmetric algorithm is AES-128, AES-192, and AES-256. All AES algorithms uses the block size of 128-bit but different size of key lengths (128, 192, 256).
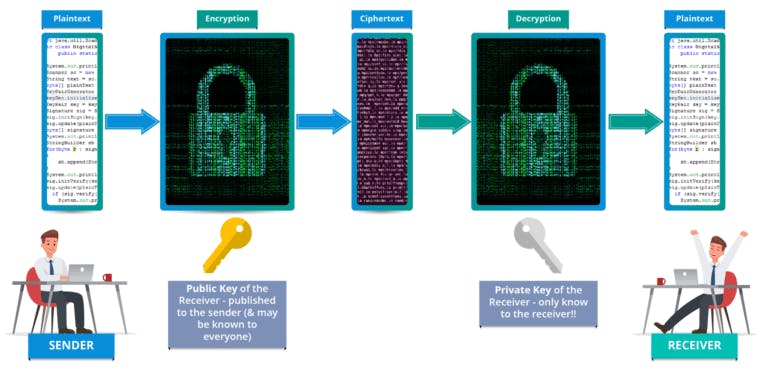
Asymmetric Key Encryption (or Public Key Cryptography)
Asymmetric cryptography uses a key pairs — public and private key. It works in a way, message encrypted with either public or private key can only be decrypted using the other key of the pair. That is public key to encrypt, private key to decrypt and private key to encrypt, public key to decrypt. Public keys are disseminated in public network whereas private keys are only known to the owners. This key pair cryptography differs from symmetric cryptography which uses one secret key.
RSA is the most widely used form of public key encryption, while others are ELC, Diffie-Helman key exchange, etc.
Asymmetric Cryptography has 2 usages, data encryption and digital signature.
Data Encryption
For data encryption, a sender encryptes an information with receiver’s public key. The message can only be decrypted using receiver’s private key which is only known to the receiver.
Encrypting a Message
- Sender encrypts a document with one time symmetric key. This is typically AES or DES Session Key.
- Sender encrypts the symmetric key with receiver’s public key
- Sender sends both encrypted document and key.
Decrypting a Message
- Receiver decrypts the session key using own private key.
- Receiver uses decrypted session key to decrypt the message.
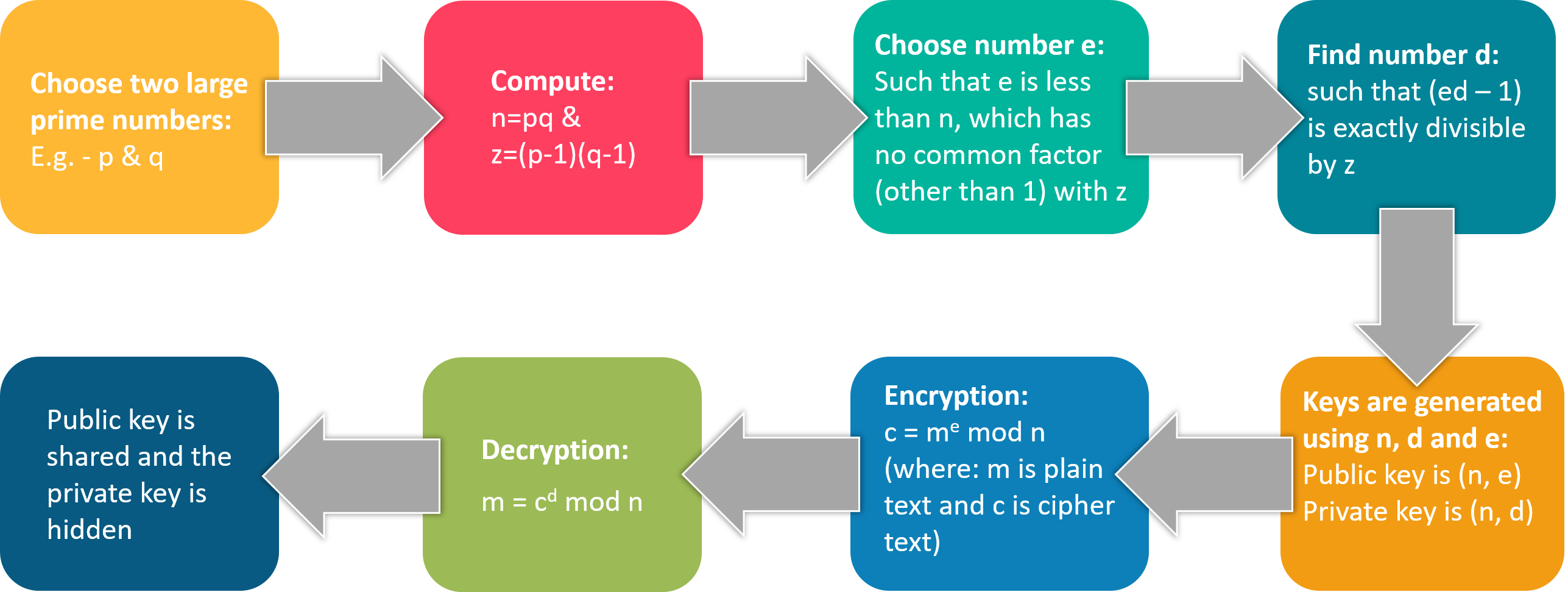
RSA Algorithm
- RSA stands for Rivest, Shamir, and Adelman, inventors of this technique
- Both public and private key are interchangeable
- Variable Key Size (512, 1024, or 2048 bits)
Here’s how keys are generated in RSA algorithm